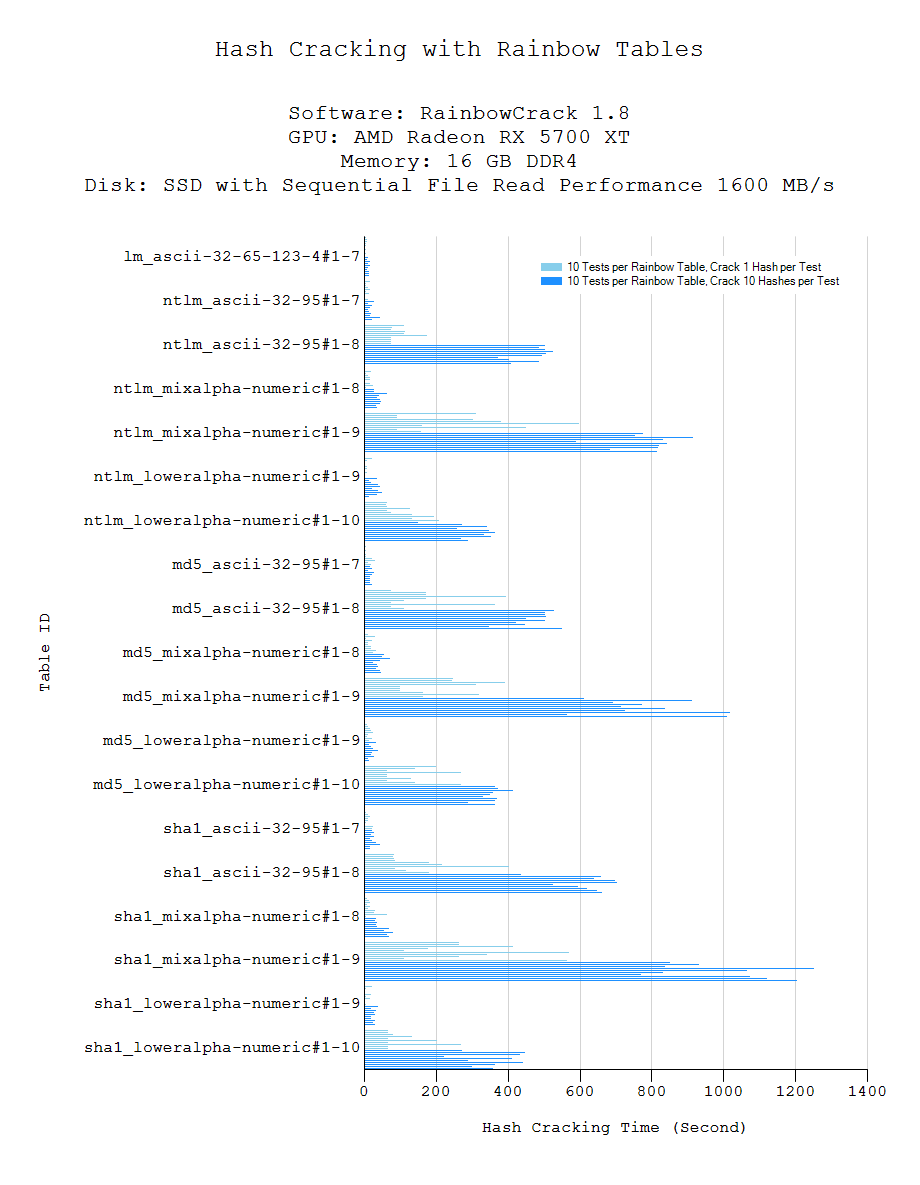
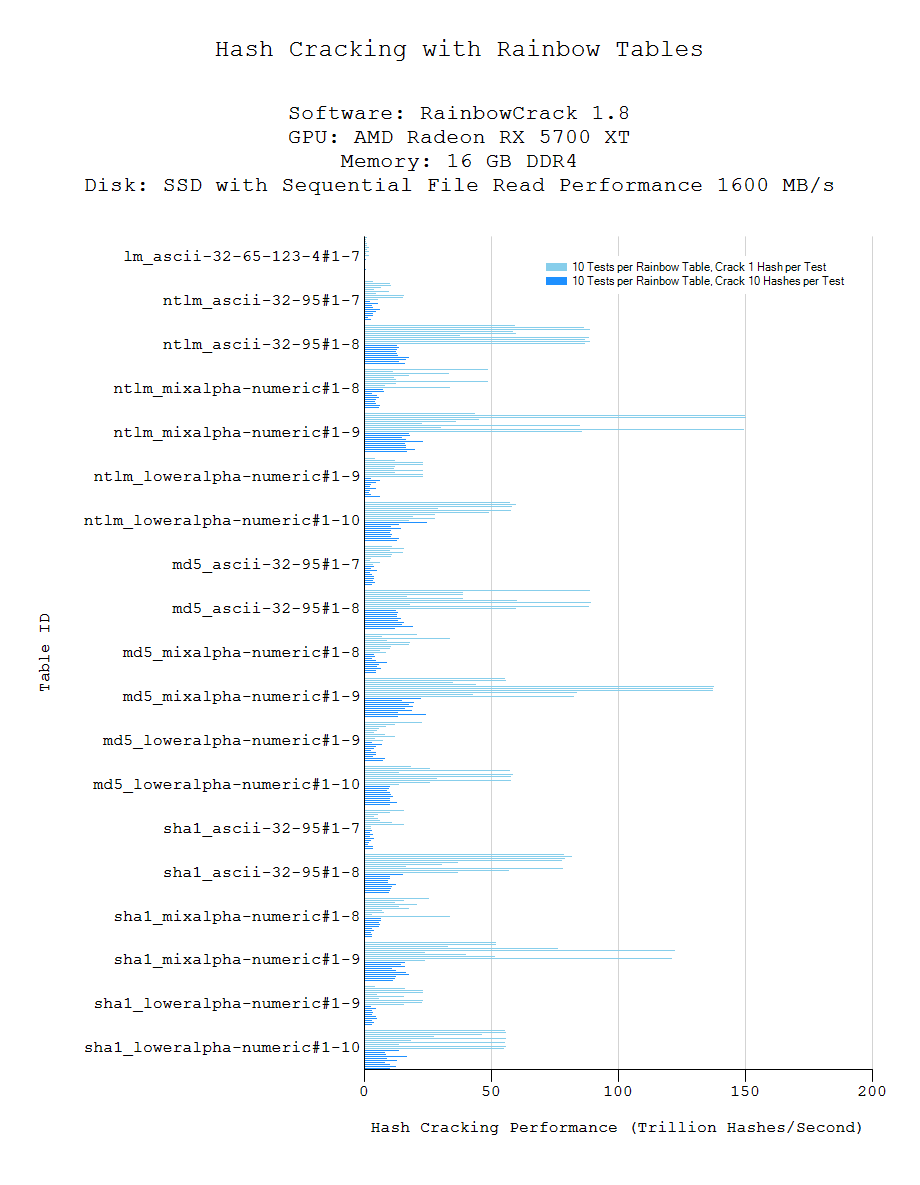
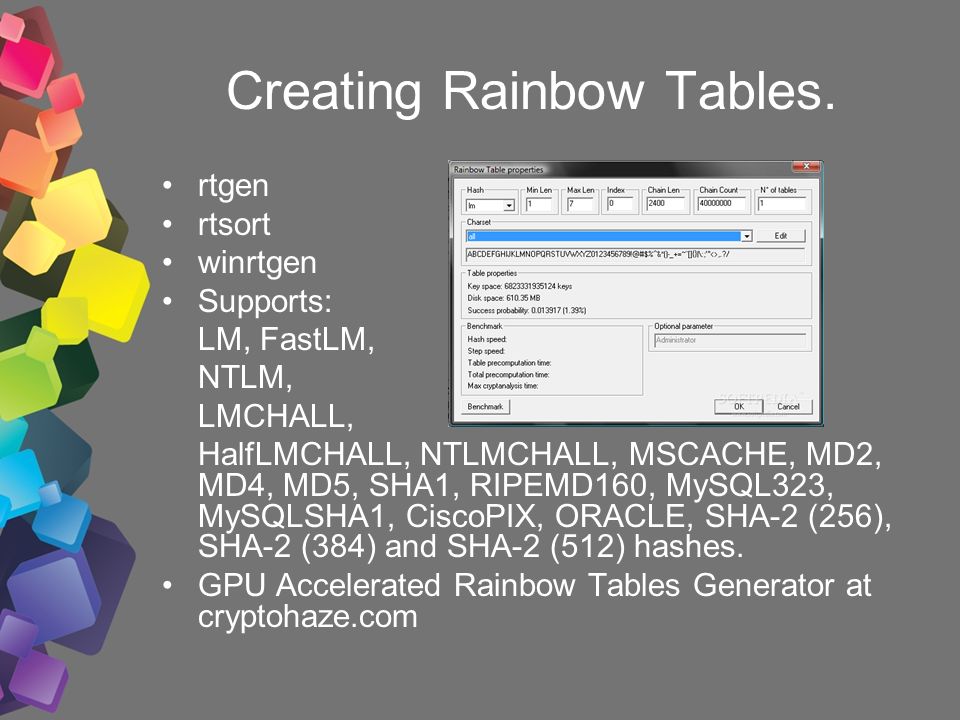
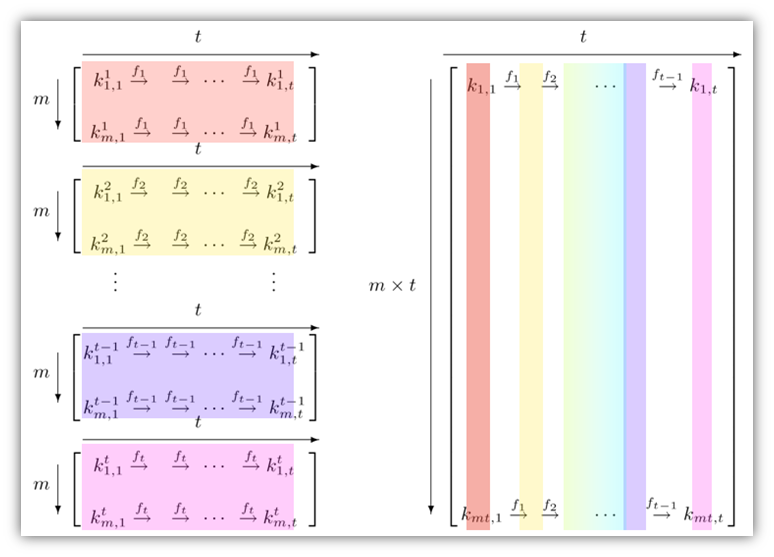
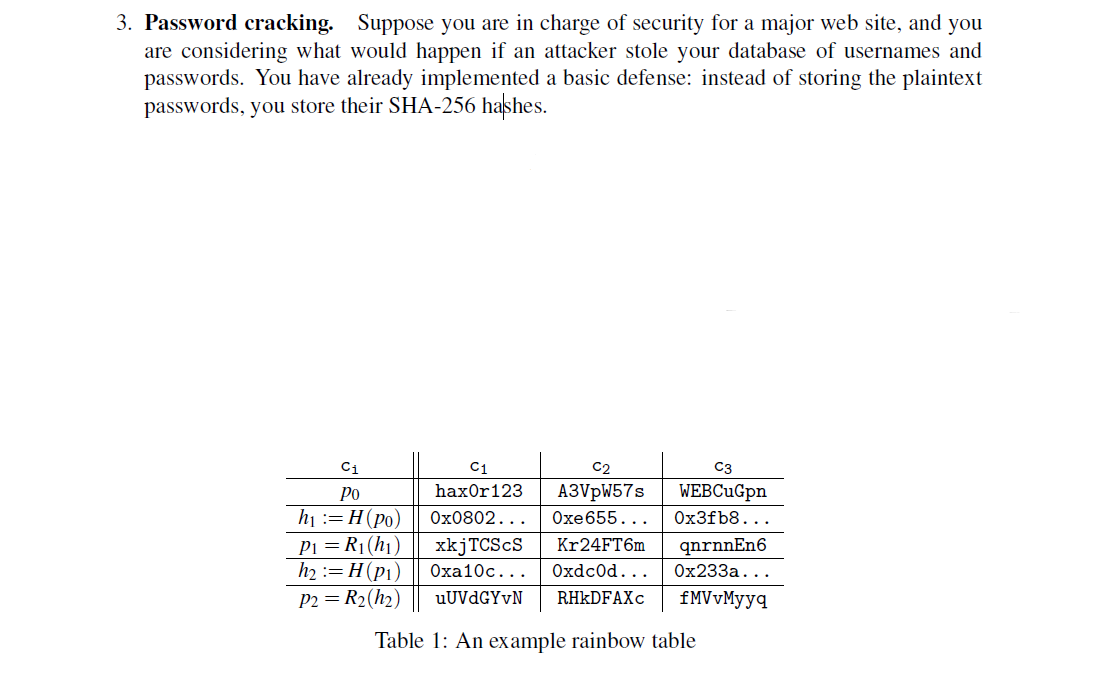
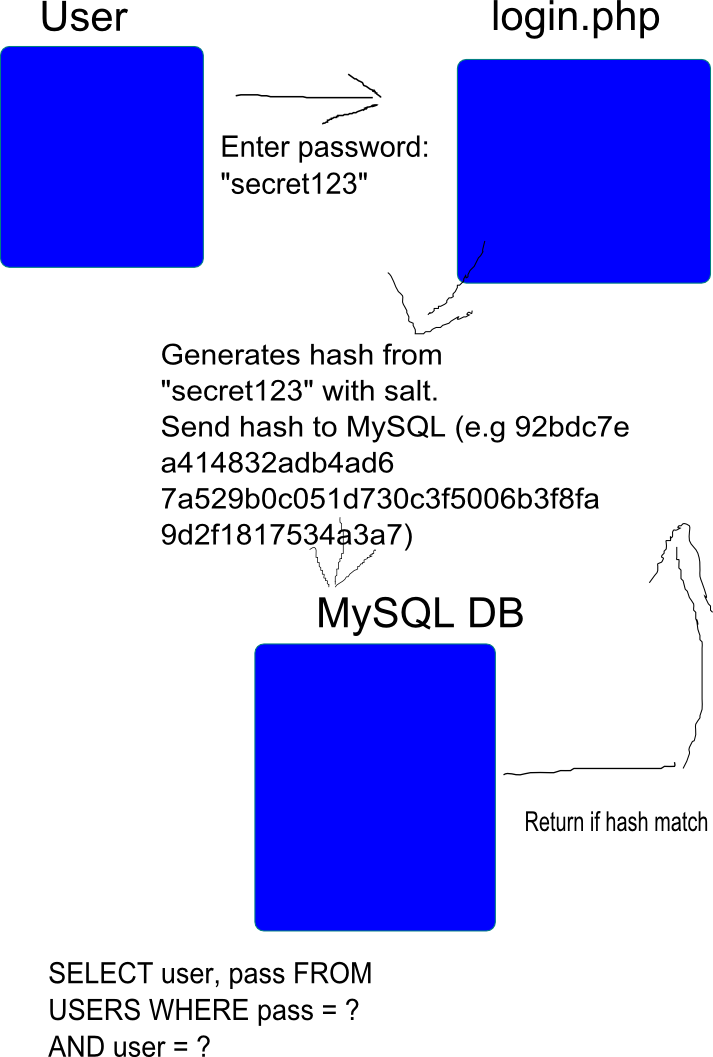
How to Create Rainbow Tables for Hashing Algorithms Like MD5, SHA1 & NTLM « Null Byte :: WonderHowTo

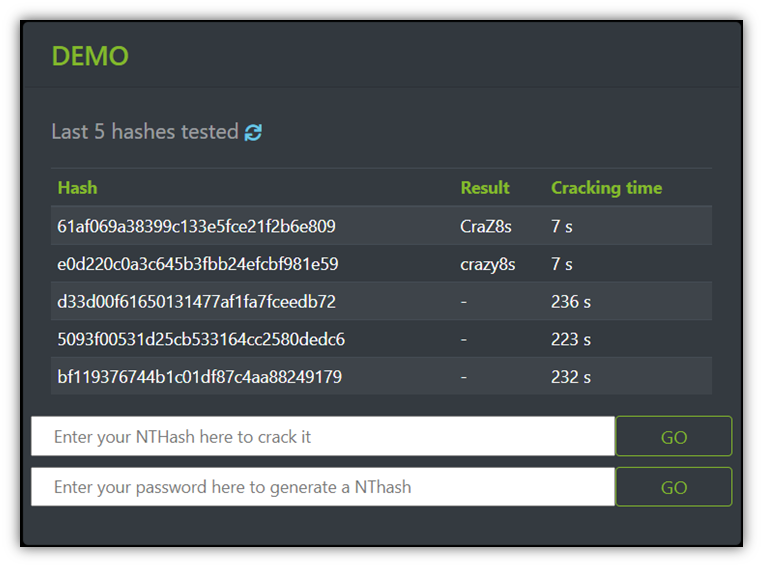
Rainbow table Attack | Password MD5, SHA1, SHA256, Salting | EP18 | Hacking | Cyber security | Tamil - YouTube
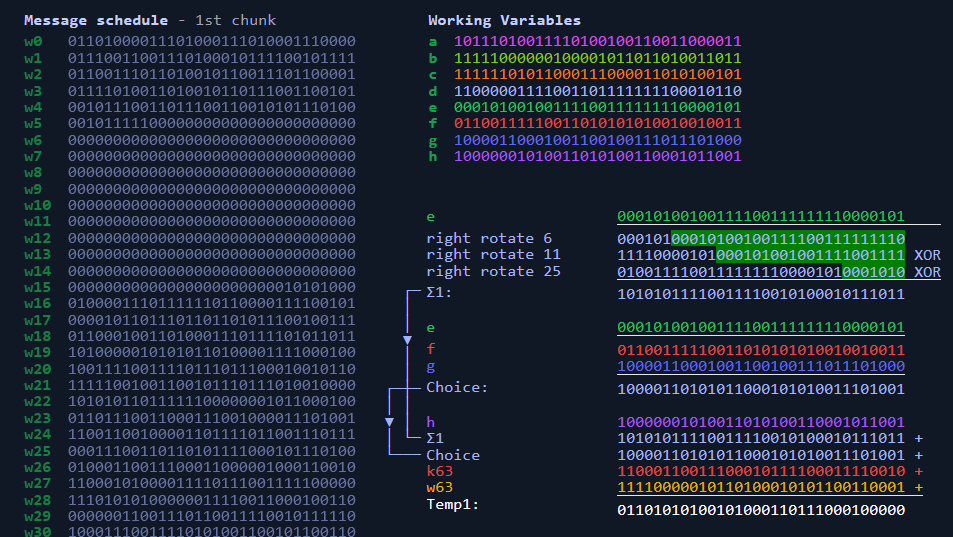
Sha256 Algorithm Explained' that visualizes the calculation process of the hash function 'SHA-256' in an easy-to-understand manner - GIGAZINE

Passwords and hacking: the jargon of hashing, salting and SHA-2 explained | Data and computer security | The Guardian
GitHub - thanosgn/rainbow-table-attack: A SHA-3 finalist hash (BLAKE) reversal using rainbow tables.